Every project or team operates differently, even within the same organization. Customizing Jira ensures that you’re capturing the right information, adhering to specific workflows, and facilitating collaboration processes efficiently for all users.
As a Jira admin, you play a pivotal role in harnessing the power of Jira and tailoring the tool to the specific needs of your users. One of the most critical aspects of administering Jira is to set up the right security and permission for appropriate access to data.
In this article, we’ll discuss security permission in Jira and how to implement it for different use cases.
Overview of Security and Permissions in Jira
Jira lets you control who can access and perform actions at the project to issue levels through permission schemes and issue security schemes. These schemes manage user access to issues and their visibility, but they don’t offer fine-grained control over field values within an issue.
Permission Schemes
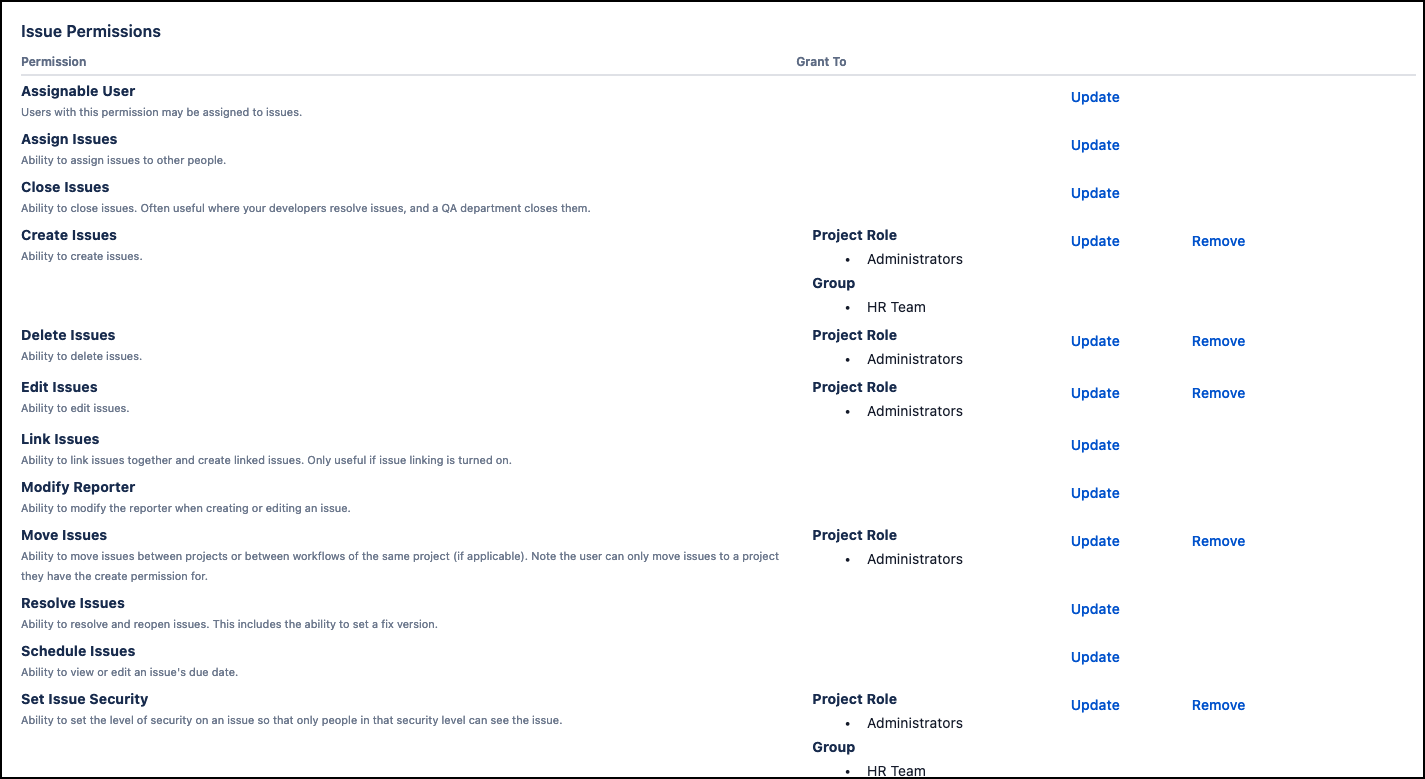
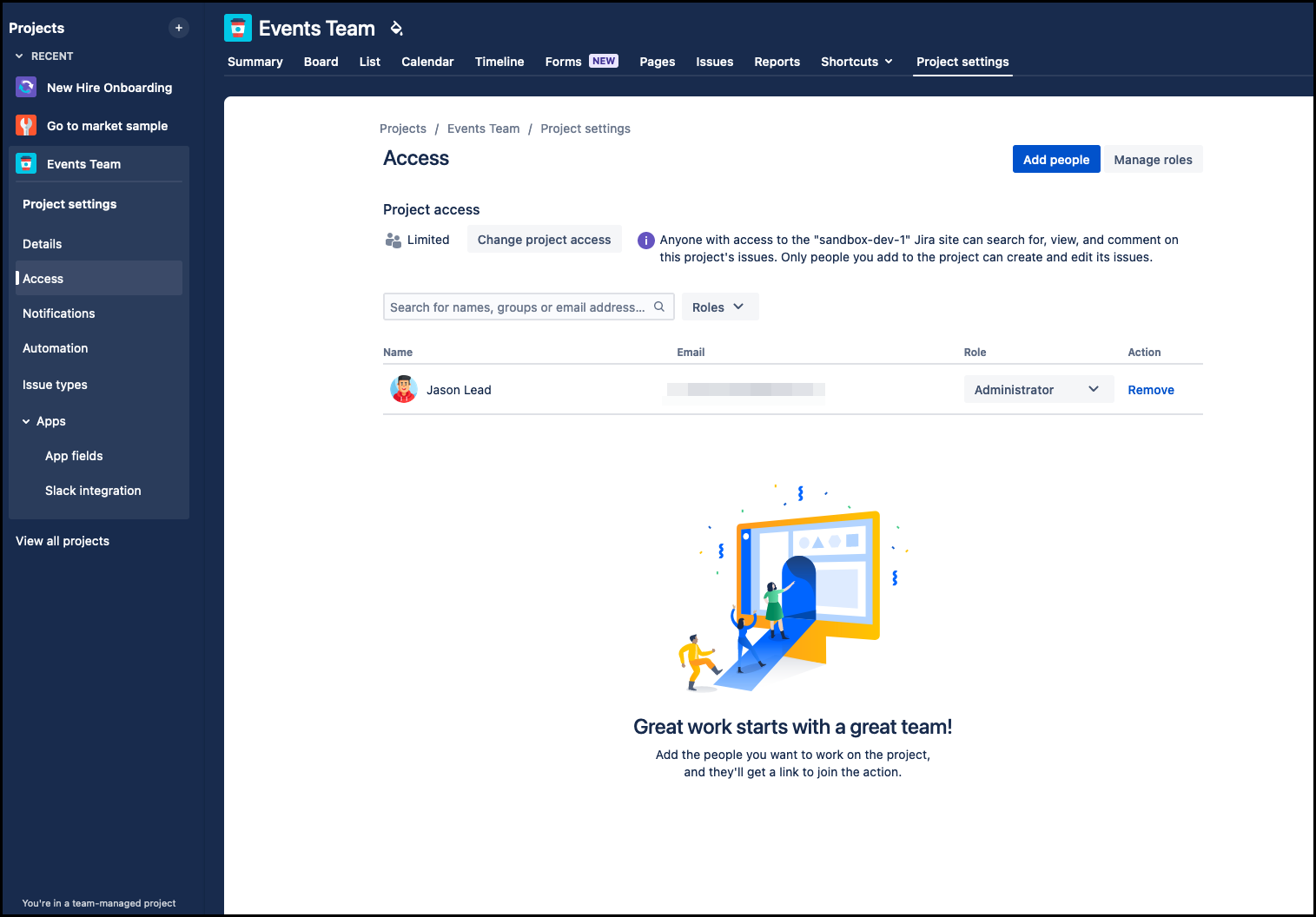
This configuration governs access to various functions and actions at both the project and issue levels. You can create and configure permission schemes that determine who has permission to edit or view issues. You can assign permission schemes to respective projects.
Tailor your permission schemes by assigning users and groups to project roles. You’ll need to define a new permission scheme and associate it with the relevant projects, typically, similar projects would share the same scheme to avoid redundancy.
Issue Security Schemes
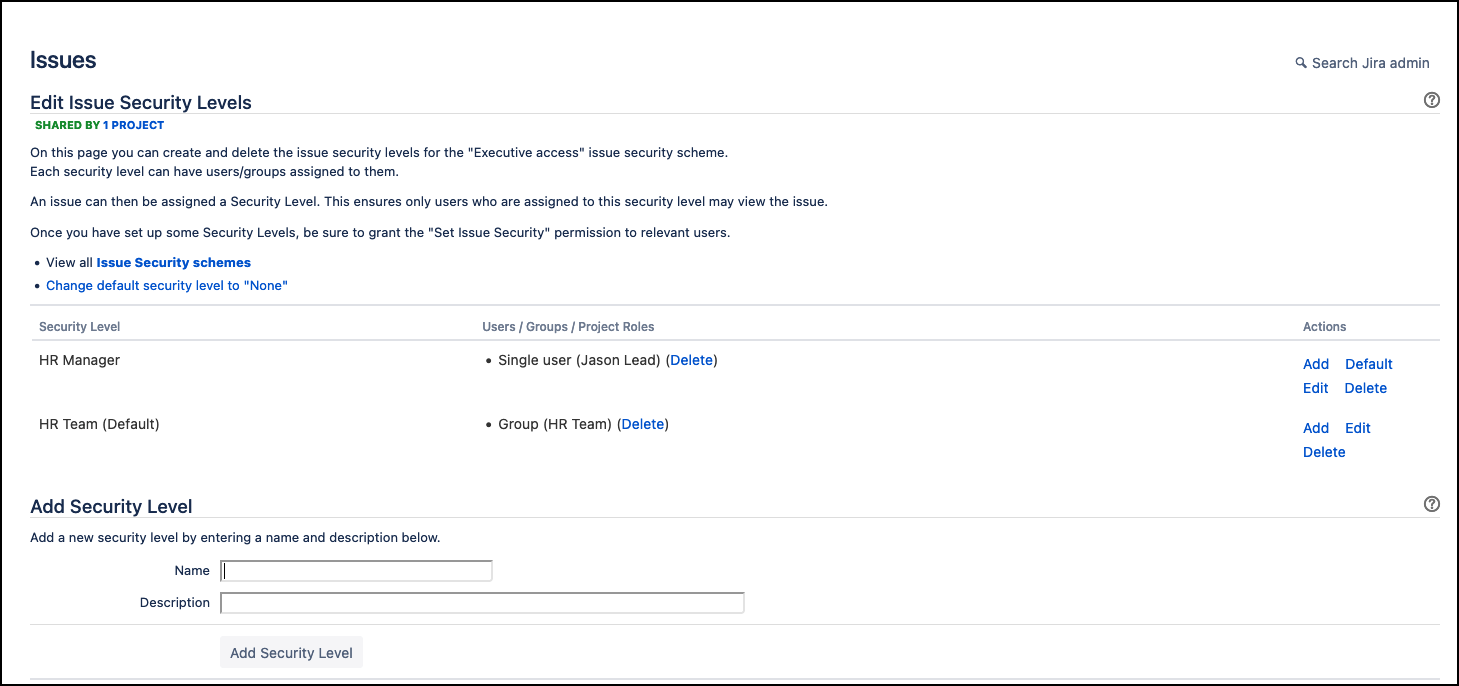
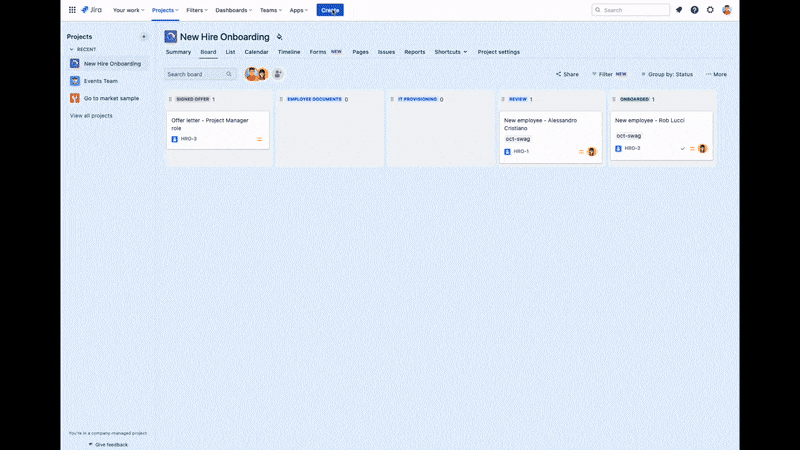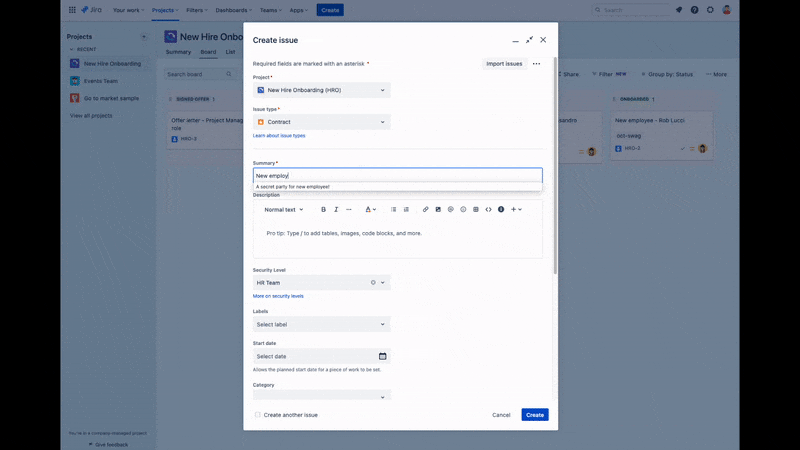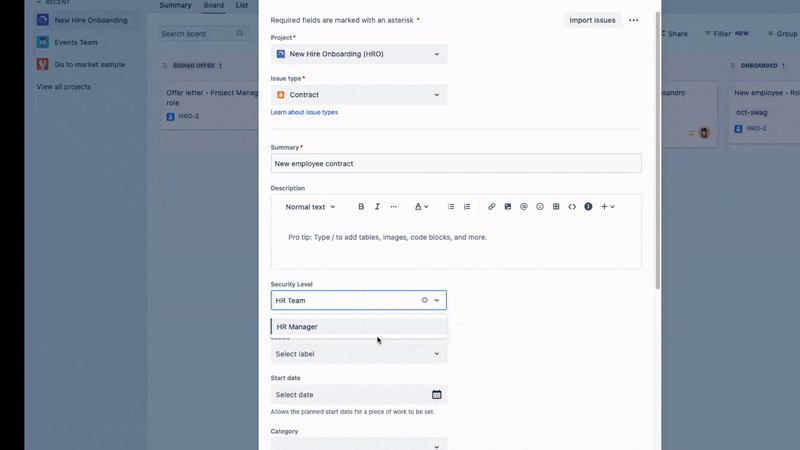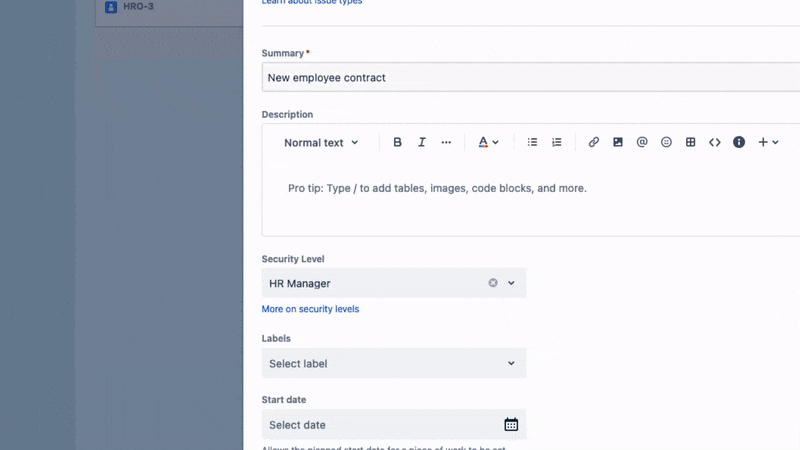
While permission schemes manage broad access, issue security schemes allow you to restrict who can view specific issues or their details. This is particularly valuable when handling sensitive or confidential data.
You can configure security levels and associate them with specific issues. Users who don’t have the necessary security level won’t be able to see the restricted information.
From the Permissions configured in the example above, we can establish additional security levels to differentiate the user’s job role.
However, this operates at the issue level and doesn’t restrict access to individual field values within an issue.
Next, let’s talk about more issue customization & configuration for different layers of security requirements.
Fields Configuration and Field-Level Security
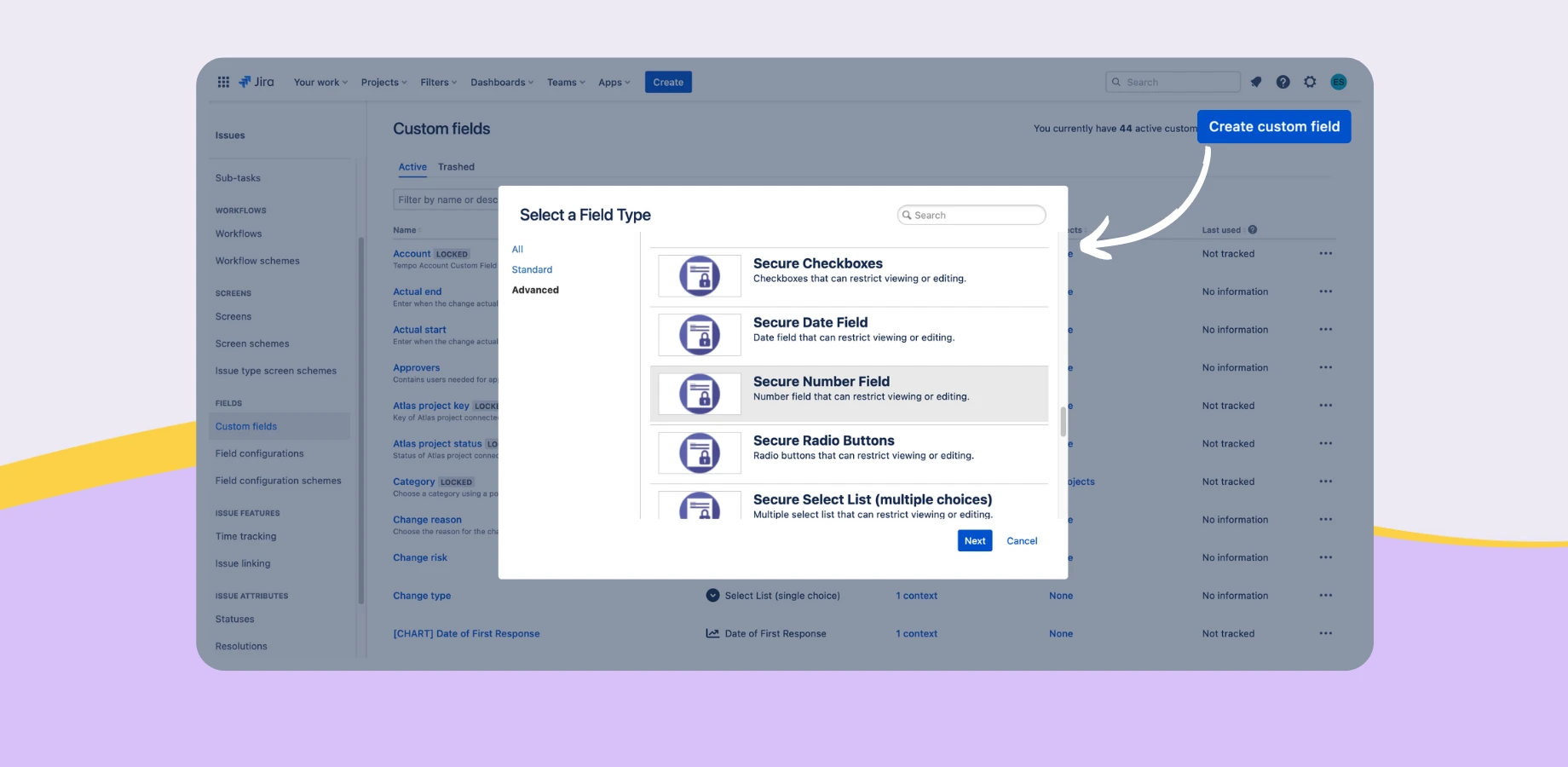
In Jira, you can also configure field-level security for custom fields. This allows you to restrict who can view or edit specific custom fields on an issue-by-issue basis. In some cases, this feature may require additional plugins or extensions.
Custom Fields and Field Behaviors
Jira allows you to create custom fields to capture specific data. You can define the behavior of these fields, including whether they are mandatory or optional, and set default values. While this doesn’t control access to the field, it does control its behavior, including whether the field is hidden or visible for a particular issue type.
Learn more: Specify field behavior | Atlassian Support
Field Context
Another simple method is to associate custom fields with specific issue types, projects, or screens. This means you can control which fields appear on which issues, but this is primarily about customizing the user interface, not restricting access to field values.
Learn more: Edit a custom field context | Atlassian Support
Automation Rules
Jira automation allows you to create rules that automate actions in response to various triggers. While you can’t directly restrict access to field values, you can use automation to enforce rules such as changing a field value based on certain criteria or triggering actions when a particular field changes.
Learn more: Edit issue fields with Jira automation | Cloud automation Cloud | Atlassian Support
Field-Level Security with Secure Custom Fields for Jira
Secure Custom Fields for Jira helps ensure that all your sensitive data is kept as secure as possible. With intuitive, easy-to-use features, users can effortlessly create, define, and configure custom fields, ultimately enabling them to securely manage and store Jira issue data, thanks to its AES-256 encryption. On top of all this, users can even seamlessly integrate the app with Jira Automation and both export and import CSV files.
While robust security measures are essential, it’s equally crucial to balance security with usability. Overly restrictive permissions can hinder collaboration and productivity. Therefore, it’s vital to regularly review and refine your security and permission configurations to ensure they align with your evolving project needs.